A system used by ships worldwide to broadcast their location for safety purposes lacks security controls and is vulnerable to spectacular spoofing attacks, researchers show.
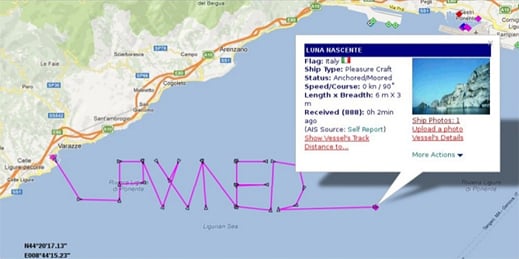 Off course:
Spoof radio signals convinced an online ship tracking service that this
fake craft had traveled on a path near Italy that spelled out the
hacker term “pwned,” which describes a system that has been compromised
by an attacker.
Off course:
Spoof radio signals convinced an online ship tracking service that this
fake craft had traveled on a path near Italy that spelled out the
hacker term “pwned,” which describes a system that has been compromised
by an attacker.A system used to track shipping vessels worldwide has been shown to be easily hijacked. Researchers found that it is possible to cause fake vessels to appear, real ones to disappear, and to issue false emergency alerts using cheap radio equipment.
Researchers with the computer security company Trend Micro discovered the problem, which stems from a lack of security controls in a technology known as Automatic Identification System, or AIS, used by an estimated 400,000 ships worldwide. Ships using the system transmit a radio signal with their location and some other details, so that other vessels and port authorities can view a map with all nearby craft shown in real time. International Maritime Organization rules make AIS mandatory on passenger vessels and on cargo ships over a certain size. Lighthouses, buoys, and other marine fixtures also transmit their location using the system.
“We were really able to compromise this system from the root level,” says Kyle Wilhoit, a researcher with Trend Micro’s Future Threat Research team. By purchasing a 700-euro piece of AIS equipment and connecting it to a computer in the vicinity of a port, the researchers could intercept signals from nearby craft and send out modified versions to make it appear to other AIS users that a vessel was somewhere it was not.
Using the same equipment and software, it is possible to force ships to stop broadcasting their movements using AIS by abusing a feature that lets authorities manage how nearby AIS transmitters operate. AIS transmissions could also be sent out that make fake vessels or structures such as lighthouses or navigational buoys appear, and to stage spoof emergencies such as a “man in the water” alert or collision warning. No direct attacks were staged on any real vessels.
The researchers showed that their spoof signals were faithfully reproduced on the maps provided by online services that monitor AIS data, such as this one. One online service was fooled into showing a real tugboat disappearing from the Mississippi and reappearing on a Dallas lake, and depicting a fake vessel traveling off Italy on a course that spelled out the hacker term for a compromised system: “pwned.”
AIS is an easy target because the signals don’t currently have any authentication or encryption mechanism, making it simple to use software to craft a signal designed to do mischief, says Marco Balduzzi, another Trend Micro researcher. “All the ships out there are affected by this problem; it’s not tied to the hardware but to the protocol.”
Ships and marine authorities also use radar to detect other vessels and obstacles. But AIS was introduced as an easier and more powerful alternative, and people have come to rely on it, says Wilhoit. Balduzzi and Wilhoit collaborated on the research with independent Italian security researcher Alessandro Pasta, and presented their findings at the Hack In the Box security conference in Kuala Lumpur on Wednesday.
The researchers attempted to notify several international marine and communication authorities, but only received a response from the International Telecommunications Union, a United Nations agency that deals with global communications policy. “They seem to be on board with changing the protocol,” says Wilhoit, “but it’s one of those foundational problems that will take time to fix.” AIS equipment has the protocol built in, so rolling out an improved form of AIS requires replacing existing equipment.
Even deciding on how to update the AIS protocol and regulations could take some time. The International Maritime Organization, another U.N. agency, is the international authority most directly responsible for AIS design and use, but a spokesperson, Natasha Brown, told MIT Technology Review that she was not aware that any research on AIS security had been presented to the agency. “This issue has not been formally raised at IMO, so there has been no [internal] discussion or IMO recommendations or guidance.”
Only a formal paper submitted via a government with IMO membership or an organization with consultative status would lead to any response, said Brown.
Marine authorities are already grappling with another navigational security challenge. In August this year, researchers from the University of Texas used spoof GPS signals to steer an $80 million yacht off course (see “Spoofers Use Fake GPS Signal To Knock a Yacht Off Course”).
http://www.technologyreview.com/news/520421/ship-tracking-hack-makes-tankers-vanish-from-view/
No comments:
Post a Comment